- /
- /
- /
Blocking External Client DNS Queries
This procedure configures the firewall to block DNS requests to servers outside the local network. With no other accessible DNS servers, clients are forced to send DNS requests to the DNS Resolver or DNS Forwarder on AZTCO-FW software for resolution.
Note: Blocking is effective but does not gracefully handle the situation. Clients must manually adjust their configura- tion to use the firewall for DNS. Redirecting DNS requests to the firewall is a more seamless solution. See Redirecting Client DNS Requests for details.
- Navigate to Firewall > Rules, LAN tab
- Create the block rule as the first rule in the list:
- Click
Add to create a new rule at the top of the list
- Fill in the following fields on the rule:
- Action: Reject
- Interface: LAN
- Protocol: TCP/UDP
- Destination: Any
- Destination Port Range: DNS (53)
- Description: Block DNS to Everything Else
- Click
- Create the pass rule to allow DNS to the firewall, above the block rule:
- Create the block rule as the first rule in the list:
Click Add to create a new rule at the top of the list
- Fill in the following fields on the rule:
- Action: Pass
- Interface: LAN
- Protocol: TCP/UDP
- Destination: LAN Address
- Destination Port Range: DNS (53)
- Description: Pass DNS to the Firewall
- Click
Apply Changes to reload the ruleset
- Fill in the following fields on the rule:
When complete, there will be two rule entries that look like the following picture:
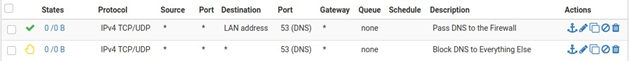
Certain local PCs could be allowed to use other DNS servers by placing a pass rule for them above the block rule.
