- /
- /
- /
Configure Configuration Synchronization (XML-RPC)
| Warning: Configuration synchronization must only be configured on the primary node. Never activate options in this section on the secondary node of a two-member cluster. |
On the primary node only, perform the following:
- Navigate to System > High Avail Sync
- Set Synchronize Config to IP to the Sync interface IP address on the secondary node, 172.16.1.3
- Set Remote System Username to admin.
Note: This must be admin, or the same user on both nodes with the “System – HA node sync” privilege
- Set Remote System Password to the admin user account password, and repeat the value in the confirmation box.
- Check the boxes for each area to synchronize to the secondary node. For this guide, as with most configurations, all boxes are checked. The Toggle All button may be used to select all of the options at once, rather than selecting them individually.
- Click Save
As a quick confirmation that the synchronization worked, on the secondary node navigate to Firewall > Rules on the
SYNC tab. The rules entered on the primary are now there, and the temporary rule is gone.
The two nodes are now linked for configuration synchronization! Changes made to the primary node in supported areas will be synchronized to the secondary whenever a change is made.
| Warning: Do not make changes to the secondary in areas set to be synchronized! These changes will be over- written the next time the primary node performs a synchronization. |
Configuring the CARP Virtual IPs
With configuration synchronization in place, the CARP Virtual IP addresses need only be added to the primary node and they will be automatically copied to the secondary.
- Navigate to Firewall > Virtual IPs on the primary node to manage CARP VIPs
- Click
Add at the top of the list to create a new VIP.
Note: A VIP must be added for each interface handling user traffic, in this case WAN and LAN.
Type Defines the type of VIP, in this case CARP.
Interface Defines the interface upon which the VIP will reside, such as WAN
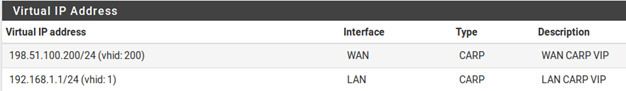
Address(es) The Address box is where the IP address values are entered for the VIP. A subnet mask must also be selected and it must match the subnet mask on the interface IP address. For this example, enter 198.51.100.200 and 24 .
Virtual IP Password Sets the password for the CARP VIP. This need only match between the two nodes, which will be handled by synchronization. The password and confirm password box must both be filled in and they must match.
VHID Group Defines the ID for the CARP VIP A common tactic is to make the VHID match the last octet of the IP address, so in this case choose 200
Advertising Frequency determines how often CARP heartbeats are sent.
Base Controls how many whole seconds elapse between Heartbeats, typically 1. This should match between cluster nodes.
Skew Controls fractions of a second (1/256th increments). A primary node is typically set to 0 or 1, secondary nodes will be 100 or higher. This adjustment is handled automatically by XML-RPC synchronization.
Description Some text to identify the VIP, such as WAN CARP VIP.
Note: If CARP appears to be too sensitive to latency on a given network, adjusting the Base by adding one second at a time is recommended until stability is achieved.
The above description used the WAN VIP as an example. The LAN VIP would be configured similarly except it will be on the LAN interface and the address will be 192.168.1.1.
If there are any additional IP addresses in the WAN subnet that will be used for purposes such as 1:1 NAT, port forwards, VPNs, etc, they may be added now as well.
Click Apply Changes after making any edits to the VIPs.
After adding VIPs, check Firewall > Virtual IPs on the secondary node to ensure that the VIPs synchronized as expected.
The Virtual IP addresses on both nodes will look like Figure CARP Virtual IP Address List if the process was successful.
Configure Outbound NAT for CARP
The next step will be to configure NAT so that clients on the LAN will use the shared WAN IP as the address.
- Navigate to Firewall > NAT, Outbound tab
- Click to select Manual Outbound NAT rule generation
- Click Save
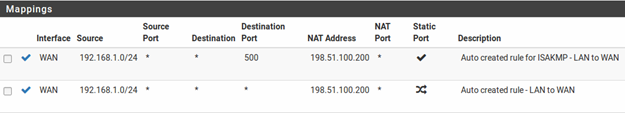
A set of rules will appear that are the equivalent rules to those in place for Automatic Outbound NAT. Adjust the rules for internal subnet sources to work with the CARP IP address instead.
- Click
to the right of the rule to edit
- Locate the Translation section of the page
- Select the WAN CARP VIP address from the Address drop-down
- Change the Description to mention that this rule will NAT LAN to the WAN CARP VIP address
| Warning: If additional local interfaces are added later, such as a second LAN, DMZ, etc, and that interface uses private IP addresses, then additional manual outbound NAT rules must be added at that time |
When complete, the rule changes will look like those found in Outbound Nat Rule for LAN with CARP VIP
Modifying the DHCP Server
The DHCP server daemons on the cluster nodes need adjustments so that they can work together. The changes will synchronize from the primary to the secondary, so as with the VIPs and Outbound NAT, these changes need only be made on the primary node.
- Navigate to Services > DHCP Server, LAN* tab.
- Set the DNS Server to the LAN CARP VIP, here 192.168.1.1
- Set the Gateway to the LAN CARP VIP, here 192.168.1.1
- Set the Failover Peer IP to the actual LAN IP address of the secondary node, here 192.168.1.3
- Click Save
Setting the DNS Server and Gateway to a CARP VIP ensures that the local clients are talking to the failover address and not directly to either node. This way if the primary fails, the local clients will continue talking to the secondary node.
The Failover Peer IP allows the daemon to communicate with the peer directly in this subnet to exchange data such as lease information. When the settings synchronize to the secondary, this value is adjusted automatically so the secondary points back to the primary.
