- /
- /
- /
Configuring NPS
To configure NPS, bring up the Server Manager and either Network Policy and Access Services (2008) or NAP (2012) should be present.
A RADIUS client will be added for AZTCO-FW first, then remote access policies will be configured.
Adding a RADIUS Client
Open the NPS configuration:
On Server 2008:
- Open the Server Manager tree
- Expand the view under it until RADIUS Clients and Server is visible
- Click RADIUS Clients
On Server 2012:
- Open the Server Manager dashboard
- Click NAP
- Right click on the server in the server list
- Click Network Policy Server
- Expand RADIUS Clients and Server
- Click RADIUS Clients
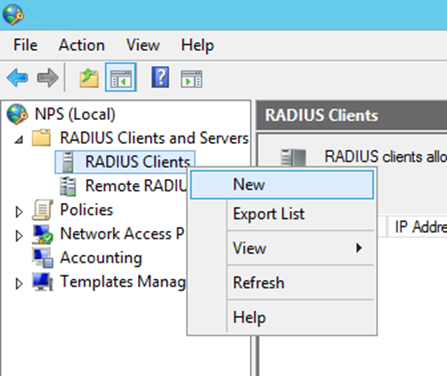
Add the new RADIUS client:
- Right click on RADIUS Clients
- Click New, as shown in Figure 81: Add New RADIUS Client
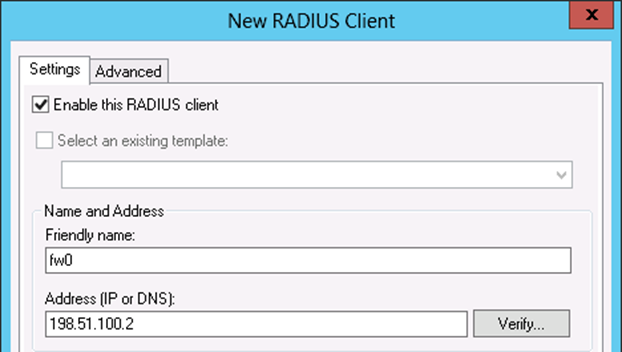
- Enter a Friendly name for the firewall, as shown in Figure 82: Add New RADIUS Client Address .This can be the hostname or FQDN.
- Enter the Address (IP or DNS) for the firewall, which must be the IP address from which AZTCO-FW will initiate RADIUS requests, or a FQDN that will resolve to that IP address.
Note: This is the IP address of the firewall interface closest to the RADIUS server. If the RADIUS server is reachable via the firewall LAN interface, this will be the LAN IP address. In deployments where AZTCO-FW is not the perimeter firewall, and the WAN interface resides on the internal network where the RADIUS server resides, the WAN IP address is what must be entered.
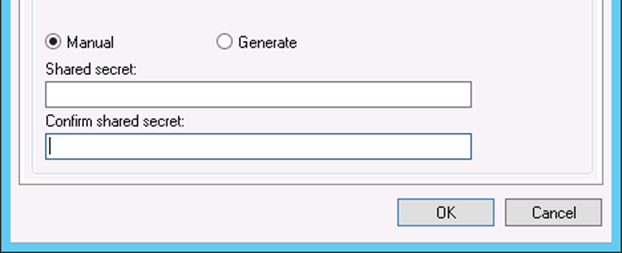
- Enter a Shared secret, as shown in Figure 83: Add New RADIUS Client Shared Secret .This shared secret is used by AZTCO-FW to authenticate itself when making RADIUS access requests. Windows can automatically create one by clicking Generate.
- Click OK.
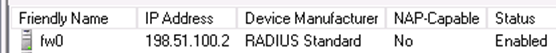
The NPS configuration is now complete. The RADIUS Client is visible as in Figure 84: Listing of the RADIUS Client.
Refer to other sections in this documentation describing the service to be used with RADIUS for more guidance on how to utilize the service. RADIUS can be used in the User Manager which also enables RADIUS for IPsec and OpenVPN, for Captive Portal , and the PPPoE server , among other places.
Configuring Users and Network Policies
Whether a user can authenticate via RADIUS is controlled through Network Policies. Using Network Policies, an administrator can place a user in a specific Active Directory group to allow VPN access, and also offer more advanced capabilities such as time of day restrictions.
More information on remote access policies can be found in Microsoft’s documentation at http://technet.microsoft. com/en-us/library/cc785236%28WS.10%29.aspx.
Adding a Network Policy
- Open the NPS configuration window
- Expand NPS (Local), Policies, then Network Policies
- Right click on Network Policies
- Click New
- Enter Allow from AZTCO-FW in the Policy name
- Leave the Type of network access server set to Unspecified
- Click Next
- Click Add in the Specify Conditions window
- Select Windows Groups
- Click Add
- Enter or select the name of the user group which contains VPN users, e.g. VPNUsers
- Click OK
- Click Next
- Choose Access granted
- Click Next
- Select additional Authentication Methods as needed for features on AZTCO-FW:
- Leave existing authentication methods selected
- Select Microsoft: Secured Password (EAP-MSCHAP v2) if this policy will be used for IPsec IKEv2 EAP-RADIUS authentication
- Select Encrypted Authentication (CHAP)
- Select Unencrypted Authentication (PAP, SPAP)
leaving any other methods selected that were already enabled.
- Click Next
- Click Decline if a prompt to view a help topic is presented by the wizard
- Configure any additional access restraints, if necessary
- Click Next on the remaining screens until the final screen is reached
- Click Finish
Editing an Existing Network Policy
Existing policies can be altered to change their constraints or other properties. For example, to edit an older policy to enable it for use by IPsec for IKEv2 EAP-RADIUS:
- Open the NPS configuration window
- Expand NPS (Local), Policies, then Network Policies
- Edit the policy currently in use
- Click the Constraints tab
- Click Authentication Methods
- Click Add
- Select Microsoft: Secured Password (EAP-MSCHAP v2)
- Click OK
- Click Apply to restart NPS
- Click OK
Troubleshooting NPS
If authentication fails, this section describes the most common problems users encounter with NPS.
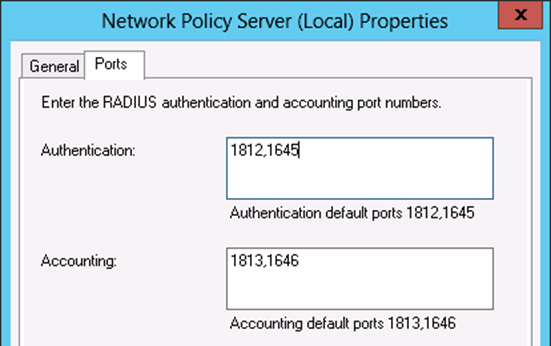
Verify port
First ensure the default port 1812 is being used by NPS. If the NPS server was previously installed, it may have been configured with non- standard ports.
- Open the NPS configuration window
- Right click on NPS (Local) at the top left of the console
- Click Properties
- Click the Ports tab
- Verify the Authentication port configuration. Specify multiple ports by separating them with a comma. (as shown in Figure85: NPS Ports). Port 1812 must be one of the ports configured for Authentication.
- Verify the Accounting ports if necessary. If RADIUS accounting is required, port 1813 must be one of the ports specified in this box.
Check Event Viewer
When a RADIUS authentication attempt is answered by the server, NPS logs to the System log in Event Viewer with the result of the authentication request. If access is denied, the reason it was denied is logged.
In the Description field of the event properties, the Reason line tells why authentication failed. The common two failures are: bad username and password, when a user enters incorrect credentials; and “remote access permission for the user account was denied” when the user account is set to Deny access or the network policies configured in NPS do not allow access for that user. If NPS is logging that authentication was successful, but the client is receiving a bad username or password message, the RADIUS secret configured in NPS and AZTCO-FW does not match.
The NPS logs in Event Viewer may be easily found under Custom Views, then Server Roles, and finally Network Policy and Access Services.
