- /
- /
- /
OpenVPN Site-to-Site Configuration Example with SSL/TLS
The process of configuring a site-to-site connection using SSL/TLS is more complicated than Shared Key. However, this method is typically much more convenient for managing a large number of remote sites connecting back to a central site in a hub-and-spoke fashion. It can be used for a site-to-site between two nodes, but given the increased configuration complexity, most people prefer to use shared key rather than SSL/TLS for that scenario.
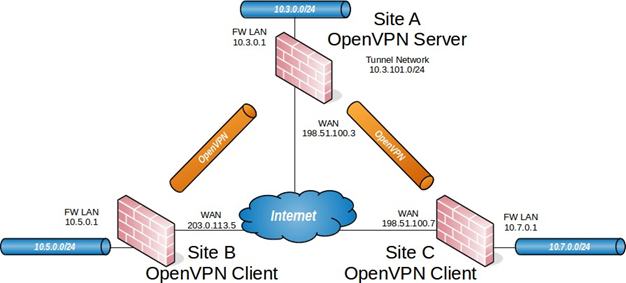
When configuring a site-to-site OpenVPN connection using SSL/TLS one firewall will be the server and the others will be clients. Usually the main location will be the server side and the remote offices will act as clients, though if one location has a static IP address and more bandwidth than the main office that may be a more desirable location for the server. In addition to the subnets on both ends there will be a dedicated subnet in use for the OpenVPN interconnection between networks. This example configuration is depicted in Figure OpenVPN Example Site-to-Site SSL/TLS Network.
- /24 is used as the IPv4 VPN Tunnel Network. The way OpenVPN allocates IP addresses is the same as for remote access clients. When using a Topology style of subnet, each client will obtain one IP address in a common subnet. When using a Topology style of net30, each connecting client gets a /30 subnet to interconnect itself with the server. See Topology for more details. The following sections describe how to configure the server and client sides of the connection. Any subnet can be used for this so long as it does not overlap any other subnet currently in use on the network.
In order for the server to reach the client networks behind each connection, two items are required:
- A route to tell the operating system that OpenVPN knows about a remote network
- An iroute in a Client-Specific Override that tells OpenVPN how to map that subnet to a specific certificate More detail on this will follow in the example.
